Digital Security
Digital Security
This is part of our Pillar Content of Flag Theory™ where we detail how you can take a well proven strategy for protecting and growing your self and your wealth apply it. The strategy is comprised of 7 flags, and Digital Security is the 6th flag – introduced in the early 2000’s. It focused on protecting your online privacy, and communicating securely without having compromises. The Snowden revelations have given new birth to the importance of this flag, and new technologies (namely digital currencies or virtual currencies) have created the need for a 7th flag (digital assets)
Essential Encrypted Services for Digital Security
- Encrypted email: Unseen.is
- Encrypted chat: Wickr, Line
- End-to-end file sharing: Unseen.is Premium, Mega.NZ
- Encrypted cloud storage: SpiderOak.com
- VPN: HideMyAss.com
Here are some of the quick and easy wins for planting a digital security flag – if you are too lazy to browse the entire list below.
Digital Security/Internet Security for the truly paranoid
- Private browsing. Duck Duck Go The search engine that doesn’t track you. A superior search experience with smarter answers, less clutter and real privacy. You can set the default preference for firefox or other browser applications to default to this preference.
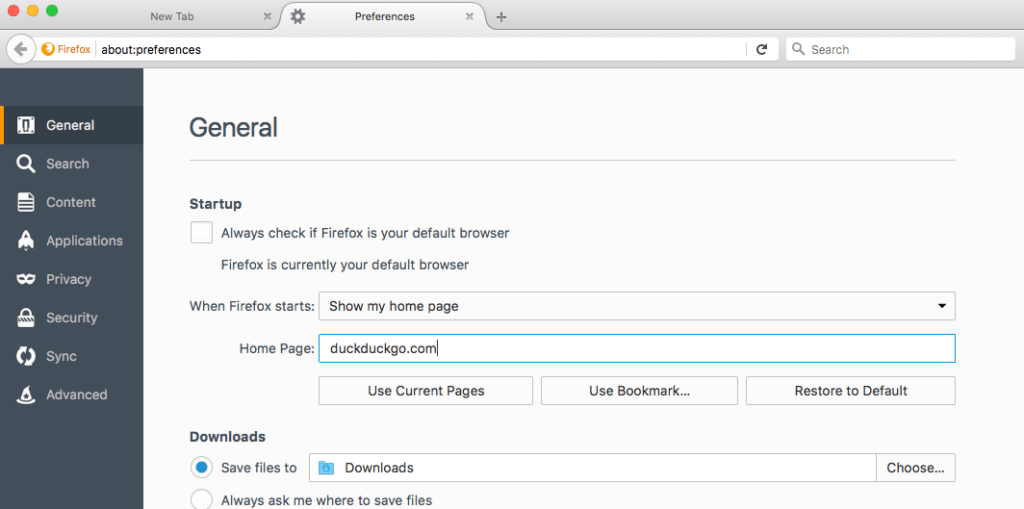
Changing your default browser settings on Firefox to set to DuckDuckGo - VPN. By using a VPN, which obscures your IP, you’ll get a more secure connection to the internet. I suggest HideMyAss, but there are many different providers who do this.
- TOR. TOR is a project that obfuscates your IP through an ‘onion’ of other connections and also makes it possible to access the Dark Web. TOR was originally started as a US Government project but has since been open-sourced and continued by proponents of freedom and privacy. [footnote]*You have to be very, very careful when accessing the dark web. There are very nefarious sites, and the FBI has even used malicious javascript injections to track down users. Proceed with caution.[/footnote]
- PGP mail. PGP uses encryption keys to encrypt and decrypt a message that can be sent over a less than secure channel. You need to exchange PUBLIC keys with the person you are sending a message to (send them this as an attachment to an email) I suggest using thunderbird and enigmail. Enigmail is a security extension to Mozilla Thunderbird that allows you to write and receive email messages signed and/or encrypted with a set of PGP keys.
- Encrypted voice and chat. There are a few programs that allow for encrypted messaging, including wicker, telegram, and more – but one I’ve found that offers voice and chat on top is unseen.is Go ahead and send our sales guy an email with your encrypted message. Here is his key for download (remember, public keys are safe to share – but private keys should never be shared).
- For PC. Spyware, malware, viruses are common if you are downloading files on a regular basis, therefore a virus scanner is a must. You likely only will come across an issue with malware if you are downloading a program, and not checking it with an up to date virus protection, unless there is an exploit in your operating system, so keep your OS up to date.
- For Mac. Little snitch – monitors your ingoing and outgoing computer traffic and allows you to control which programs are accessing the internet.
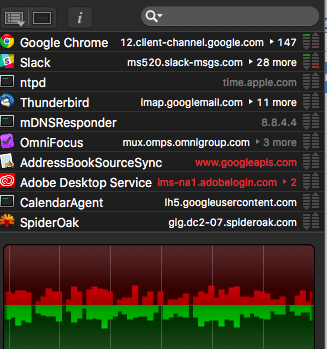
Little Snitch in action – red means the program is being stopped. - Multiple factor authentication. Dual authentication is using two factors to prove your identity. Most commonly you can pair a password with your phone and a tool like google authenticator or clef. Other more important services like banking can often allow you to get multiple factor authentication with 3 or more verifications (banking dongle, password, cell phone text message).
- Search whois records. Making a whois search is one of the easiest ways you can quickly determine who owns a site, and if that site is trustworthy. A friend who is deep into SEO even suggested that a private or anon. whois record might rank lower than public and true information.
- Anonymize your whois records. If you are the owners and you want to remain anonymous, then you can pay a firm to display their information. However, be aware that of these ‘whois privacy providers’ are will flip like a pancake under any legal pressure.
- Search companies house records. First check on Incorporations.IO to see if the information is public. Then lookup the Companies House which enables you to check out details about company addresses, owners and the like. Look for big discrepancies between onscreen addresses and physical offices.
- Choose a Private Jurisdiction for Incorporation. Because anyone can at anytime lookup the shareholder in your company if you select a jurisdiction to incorporate which makes this information public, it is advantageous to select a jurisdiction for your company which is private.
- Privately Register your Company using a nominee. Sometimes due to physical location or local laws, you need to register in a jurisdiction which publicly avails your private information. Alas, there is oftentimes ways around this and you could privately register your directors and shareholders by using a nominee.
- Be Wary of Social engineering. Scams and people trying to give you 1,409,059.93 cents from your uncle’s estate if you’ll only release to them $500 to (bank account in random developing nation) are not your friend, and did not know your uncle.
- Reverse image search images. Tineye is a website that allows you to look backwards at pictures to see where they came from. Useful in preventing human engineering, and determining if that hottie you met on the online dating site is a real date, or a honeypot sent from the KGB for counterespionage.
- Never use internet explorer. If you are using IE6, your computer is likely comprimised already. Google and YouTube have now stopped supporting the ageing browser – but it’s also riddled with security flaws. Do yourself a favour and download a newer browser.
- Virus Total. Worried about the provenance of a file? Upload it to www.virustotal.com. You’ll get a number virus-scanning engines to find any hidden malware for free.
- Don’t Use Dropbox. This company has a particularly bad reputation for sharing user data, and not providing end to end encryption “We’re talking about encryption. We’re talking about dropping programs that are hostile to privacy. For example, Dropbox? Get rid of Dropbox, it doesn’t support encryption, it doesn’t protect your private files. And use competitors like SpiderOak, that do the same exact service but they protect the content of what you’re sharing.” – Ed Snowdon
- Don’t Use Facebook. “They trust me – dumb fucks,” says Mark Zuckerberg in a text message referring to users of Facebook services who submitted personal information. Things have changed since he built Facebook in a dorm room and turned it into a multi-national company earning multiple billions in the process. However, it’s telling of the companies stance on privacy, direct from the Founder at the inception of the business. Source
-

Copy of leaked slide that shows the information that can be gathered by PRISM on request from intelligence agents. Encrypt file storage in the cloud. Don’t use dropbox. Encrypt files when you pass them to others, use Mega.NZ
Mega Upload homepage looking pretty cool. - Check site safety. Look in the search results for a malicious notification, or with www.siteadvisor.com. This is a browser plug-in that has a green, yellow and red site rating icons will help you to avoid compromised web locations. Moderately useful, normally search engines won’t display sites that have been compromised or have malware anyway.
- Test your antivirus system. Using the Eicar string (which is a string of text most virus engines use) you’ll be able to detect a virus even if it is obfuscated, wrapped or compressed.
- Use Proper Website hosting. This could be an entire article in and of itself, but most of the web runs on wordpress, and most wordpress runs on WPengine. Therefor if you are hosting a wordpress site, use WPengine. This should take care of the majority of the issues you might face, as they explicitly disallow certain plugins or themes that have been compromised.
- Use strong, multiple passwords. You should utilize a strong password generator, or use a passphrase instead of a password. A “dictionary attack” or “rainbow table” is a common attack by a hacker using an automated tool.
- Encrypt your data. I already included this, but want to mention it again, it’s that important! Use spideroak or another encryption mechanism to encrypt your hard disk or USB thumb drive. It goes without saying that if it is ever lost or stolen, whoever accesses the data won’t be able to read it if it’s encrypted.
- Careful when throwing out a computer. Magnets, freezers, fire, smashing the item to bits and pieces can provide some degree of assurance that data is destroyed, but not 100%.
- Hide your DNS….The leader in this space is OpenDNS. They were recently acquired by CISCO systems. Might be better to use open source software DNScrypt which also encrypts your data.
- Take care on public networks. Hotspots (particularly airports, hotels, coffee shops) are the most vulnerable places you can access the internet. While it might be convenient to use public wifi, you may be exposing yourself to a MITM attack. A man in the middle attack is where a person builds a bridge between your computer the router you are connecting to, stealing the datapackets you are sending to the router. Basically the person will impersonate the router, and then when you connect to the router, you are actually connecting to a malicious source.
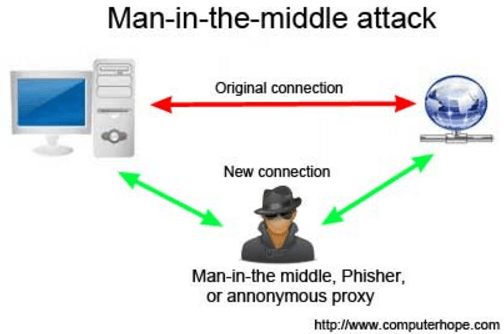
Illustration of a “MITM attack” or why you need to be careful on public wifi. - Virtualize. The truly paranoid could virtualise. This is accomplished from creating a virtual PC, using it to perform tasks, and then destroying it, along with any viruses that may have infected it while you were online. Running a virtual version of Ubuntu from within Ubuntu is likely to be the easiest way of achieving this style of computing.
- Use a credit card as opposed to a debit card. If you need a one time card, consider using a pre-paid debit card.
- Use a password Manager. This is one where I am conflicted, as password managers do help save time, but ultimately you are providing a lot of data to a single point of failure. If that company gets hacked (as notably, lastpass did) then you might be doing a lot of password changes to make sure you are safe again.
- Prevent Trackers. There are many different tracker blockers out there. But Blur, is one that tries to do everything. According to their site, it is the only Password Manager that secures your email, phone, and credit card and prevents tracking.
- Use cookie management software or incognito mode to ditch cookies for big sites that you don’t want to be tracked by (Youtube, Google, Amazon, etc.)- Be sure to clear your cache!
- Use Fluid App (paid for, $5) for creating a site-specific browser with separate cookie storage for websites that you access regularly and can’t avoid being tracked by (Facebook, Gmail, etc), or just for web apps you use a lot and want to access via alt-Tab (BitBucket, Trello, etc).
- Use ssl. Both as a business owner, and as a host – SSL gives more confidence. SSL stands for secure socket layer, and you can buy a certificate for very cheap (even free).
- Use Cloudflare with sites that you host. Cloudflare helps mitigate against a DDOS attack. If you are a website owner, you make money when your site is online. A DDOS attack is a distributed denial of service attack. This is essentially *many* different connections to your site simultaneously, initiated by a bad actor in an attempt to overwhelm your hosting provider.
- A diagram of what a DDOS attack looks like.
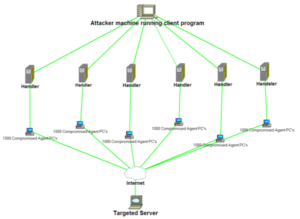
Diagram of a DDOS attack. - Make sure you’re using dnssec on all your own domains – it will protect against DNS based attacks and some mitm attacks
- Email Tips from your own domain. Setup spf records and dkim for all your domains – it will stop/slow down people spoofing email from your domain
- Don’t Use Hushmail! Hushmail uses PGP as a protocol, which is safe, but unfortunately have been known to flip on their customers due to pressure from government. Notably, they created an insecure Java applet with a backdoor to intelligence agencies so the agencies could steal their own customers passwords.It’s complicated and the details are hazy – but some investigative reporting pretty much confirmed this rumor. It involved a password vulnerability on the server side that wasn’t exposed on the client side, but the TL;DR is PGP is safe – but don’t use hushmail! Better to do it yourself 100% client side or use a more reputable provider.http://www.theregister.co.uk/2007/11/08/hushmail_court_orders/
- Unregistered / throwaway data SIMs. Many countries allow for SIM’s to be obtained without any identification (see panama). Some require a passport to signup (see Thailand) and others require a plethora of data including Tax ID (see Brazil). You might also consider the phone you are using – and use a “burner” or throwaway phone if you are particularly paranoid.
- Second Passport. Obtain a second passport – The 1st Flag of Flag Theory and use this identification as needed.
- Tax Residency. Properly establish a legal tax residency in a private, low tax jurisdiction – The 2nd Flag of Flag Theory and ALWAYS set your VPN location to this country.
- Offshore company. Utilize an Offshore Company to hold assets, and ALWAYS register web domains, hosting, and assets of the company properly within this legal entity.
- Bank in Private Jurisdiction. Unfortunately, banking isn’t as private as it used to be. As of 2016, the most private place to setup a bank account is actually the USA. but pair that with a Wyoming company and no one but the IRS will be able to find out without a lawsuit.
- Buy Gold and Physical Assets – Plant them in a secure, offshore and safe jurisdiction like Singapore, Switzerland and you’ve effectively planted the 5th Flag of Flag Theory.
- Utilize this very list! The 6th Flag of Flag Theory
- Use CryptoCurrency – The 7th Flag of Flag Theory.
Why is Digital Security Necessary?

There are countless examples of how governments around the world, particularly the “5 eyes” have overstepped bounds and see it as important and necessary to collect as much data as possible. This data is being held in massive data centers for an indefinite period of time. So even if what you are don’t isn’t illegal (now) it can still be used against you later down the road. This isn’t a crazy conspiracy theory, these are facts.
This is a very slippery slope indeed. We now live in a  world where a simple google search could implicate you in a crime, or at least deny you of bail under certain circumstances.
world where a simple google search could implicate you in a crime, or at least deny you of bail under certain circumstances.
- If you google search”how to get away with murder” does that make you a murder?
- If you read a book on “how to avoid taxes?” does that make you a tax evader?
- If you search “how to start a fire?” – does that make you a arsonist?
- If you google “how to explore space?” Will a magical jetpack suddenly appear and take you to outer space?
Obviously the answers to these questions are no. However, the are courts that have held people without bail because of these types of internet searches. A million abstractions can be drawn by the courts about intention. However, as evidenced by the above, intention does not equal action.
This is a perverted form of future crime, Minority Report style, and it brings up a scary conclusion: When governments and corporations collude to provide your private information, it can and will be used against you in a court of law. It’s clear that there is a necessary action to be taken to protect ourselves in our homes, and in our laptops – to secure the privacy of our most personal intentions.
It’s a natural human right, and anyone who tells you that they “have nothing to hide” is offering up a straw-man’s argument. The argument isn’t whether you have something to hide, it’s whether we as humans have the right to be safe and secure in our personal space. In America (home to the most egregious violators of privacy rights on both corporate and public level) citizens should are no longer protected by the 4th Amendment of the constitution.

[t]he right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.
I feel it fitting to end the article with a quote from one of the drafters of the constitution document, Benjamin Franklin: “Those who would give up essential Liberty, to purchase a little temporary Safety, deserve neither Liberty nor Safety.”



